Introduction to HashiCorp Boundary Enterprise 0.18.0
HashiCorp Boundary Enterprise 0.18.0 represents the latest milestone in secure access management, providing organizations with a comprehensive solution to manage access to critical resources across dynamic, hybrid, and multi-cloud environments. This full version release introduces robust features designed to enhance security, scalability, and ease of use. Activated with cutting-edge capabilities, HashiCorp Boundary Enterprise empowers enterprises to establish secure perimeters and seamlessly control access to applications and infrastructure.
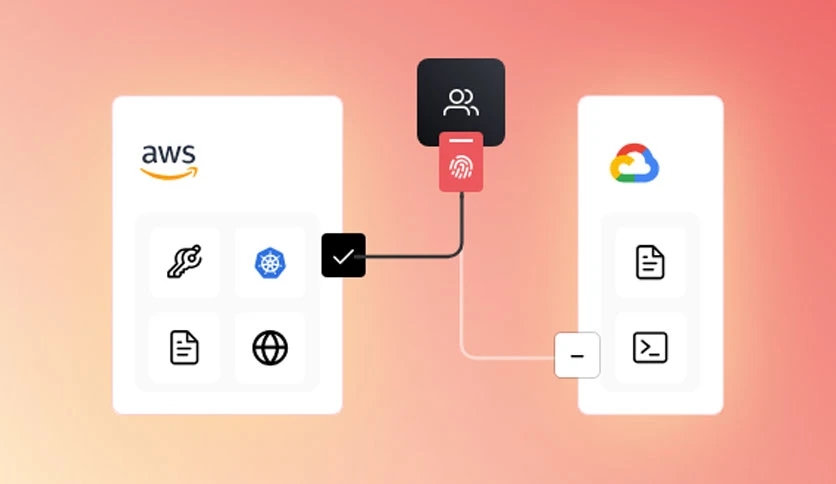
With an emphasis on fine-grained access controls, HashiCorp Boundary Enterprise 0.18.0 delivers a sophisticated yet intuitive platform for managing privileged access. This pre-activated release ensures that organizations can quickly deploy and benefit from advanced security measures, addressing the evolving challenges of modern IT landscapes. As organizations strive for a balance between user flexibility and security, HashiCorp Boundary Enterprise emerges as a key player in facilitating secure access to resources, streamlining workflows, and safeguarding critical assets.
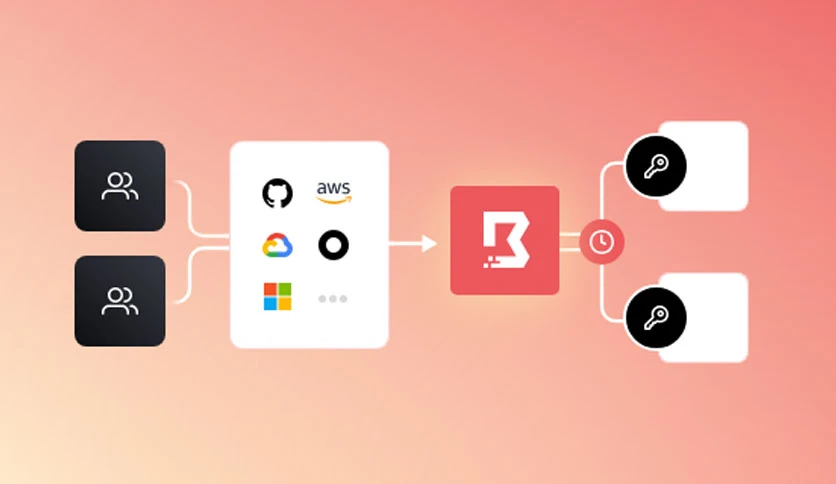
Key Features of HashiCorp Boundary Enterprise 0.18.0
1. Fine-Grained Access Controls
HashiCorp Boundary Enterprise 0.18.0 introduces an enhanced access control model, allowing organizations to define and enforce precise access policies based on user attributes, resource characteristics, and contextual information. This ensures that only authorized users gain access to specific resources, bolstering overall security.
2. Dynamic Authorization
The dynamic authorization feature enables organizations to adapt access permissions in real-time based on changing circumstances. Whether responding to incidents, scaling infrastructure, or adjusting user roles, HashiCorp Boundary Enterprise provides a flexible and responsive authorization framework.
3. Multi-Cloud Support
HashiCorp Boundary Enterprise 0.18.0 extends its reach across multi-cloud environments, allowing organizations to seamlessly manage access controls in complex, distributed architectures. This feature simplifies access management for applications and resources deployed across diverse cloud platforms.
4. Role-Based Access Management (RBAC)
RBAC capabilities in HashiCorp Boundary Enterprise facilitate the implementation of access controls based on predefined roles and responsibilities. This ensures a standardized and efficient approach to managing access permissions, reducing the risk of human errors and unauthorized access.
5. High Availability and Scalability
With a focus on enterprise-grade reliability, HashiCorp Boundary Enterprise 0.18.0 incorporates high availability features, ensuring uninterrupted access control operations even in the face of infrastructure failures. Scalability enhancements accommodate the dynamic growth of organizations and their evolving access management needs.
6. Centralized Policy Management
HashiCorp Boundary Enterprise centralizes the management of access policies, providing administrators with a unified interface to define, modify, and audit access controls. This streamlined policy management enhances operational efficiency and reduces the complexity of access governance.
7. Secure Remote Access
As remote work becomes increasingly prevalent, HashiCorp Boundary Enterprise prioritizes secure remote access solutions. The platform ensures that users can securely connect to corporate resources without compromising security, irrespective of their location or the network they are using.
8. Audit and Compliance Reporting
To meet regulatory requirements and internal compliance standards, HashiCorp Boundary Enterprise 0.18.0 includes comprehensive audit and reporting features. Organizations can generate detailed reports on access activities, aiding in compliance audits and security assessments.
System Requirements
Server Requirements:
– Operating System: Linux (Kernel 3.10 or later), Windows Server 2016 or later
– CPU: Quad-core 2.5 GHz or higher
– RAM: 8 GB or more
– Storage: 50 GB of free disk space
Client Requirements:
– Operating System: Windows 10, macOS 10.14 or later, Linux (64-bit)
– RAM: 4 GB or more
– Disk Space: 20 GB of free disk space
– Network: Stable internet connection
FAQs
Q: Is HashiCorp Boundary Enterprise 0.18.0 available as a pre-activated version?
A: Yes, HashiCorp Boundary Enterprise 0.18.0 comes as a pre-activated full version, enabling organizations to deploy and utilize its advanced features without additional activation steps.
Q: Can HashiCorp Boundary Enterprise support multi-cloud environments?
A: Absolutely, HashiCorp Boundary Enterprise 0.18.0 is designed to seamlessly support multi-cloud environments, providing unified access controls for resources distributed across various cloud platforms.
Q: How does the dynamic authorization feature benefit organizations?
A: The dynamic authorization feature in HashiCorp Boundary Enterprise allows organizations to adjust access permissions in real-time, offering flexibility in responding to incidents, scaling infrastructure, and adapting to changing user roles.
Q: What is the role of RBAC in HashiCorp Boundary Enterprise?
A: Role-Based Access Management (RBAC) in HashiCorp Boundary Enterprise simplifies access control by allowing organizations to define access permissions based on predefined roles and responsibilities.
Q: How does HashiCorp Boundary Enterprise ensure secure remote access?
A: HashiCorp Boundary Enterprise prioritizes secure remote access, ensuring that users can securely connect to corporate resources from any location without compromising security.
Q: What reporting features are available for audit and compliance purposes?
A: HashiCorp Boundary Enterprise 0.18.0 includes comprehensive audit and compliance reporting features, enabling organizations to generate detailed reports on access activities for compliance audits and security assessments.